MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA
Por um escritor misterioso
Last updated 07 novembro 2024

INTRODUCTION In today’s ever-evolving cybersecurity landscape, the role of malware detection solutions has reached a critical juncture in safeguarding against

Exfiltrator-22 Framework

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Billions of Google Chrome, Microsoft Edge users warned over eerie 'Mystic' app that steals all of your money in seconds

Shadowpad Malware Report - CYFIRMA

Emotet resurgence: cross-industry campaign analysis

Researchers Uncover Packer Used by Several Malware to Evade Detection for 6 Years
Cyfirma (u/Cyfirma) - Reddit
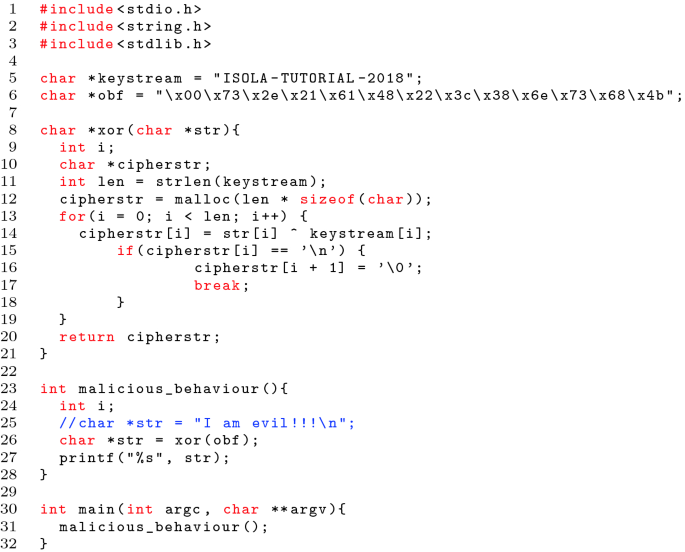
Tutorial: An Overview of Malware Detection and Evasion Techniques

Tracking the Hive: Darktrace's Detection of a Hive Ransomware-as-Service

New MaaS Prysmax Launches Fully Undetectable Infostealer - CYFIRMA

PlugX Malware: A RAT's Race to Adapt and Survive

A Survey of strategy-driven evasion methods for PE malware: Transformation, concealment, and attack - ScienceDirect
Recomendado para você
-
Evade - Roblox07 novembro 2024
-
 All controls in Evade - Roblox - Pro Game Guides07 novembro 2024
All controls in Evade - Roblox - Pro Game Guides07 novembro 2024 -
 Evade - Xbox Controller Experience07 novembro 2024
Evade - Xbox Controller Experience07 novembro 2024 -
 CONTROL How To Get Evade Ability (CONTROL A Merry Chase Side Mission)07 novembro 2024
CONTROL How To Get Evade Ability (CONTROL A Merry Chase Side Mission)07 novembro 2024 -
 US Advisory on Russian Sanctions Evasion07 novembro 2024
US Advisory on Russian Sanctions Evasion07 novembro 2024 -
 Chinese AI groups use cloud services to evade US chip export controls07 novembro 2024
Chinese AI groups use cloud services to evade US chip export controls07 novembro 2024 -
 Loveland Products - Evade 4L Prodiamine - gal – Steve Regan Company07 novembro 2024
Loveland Products - Evade 4L Prodiamine - gal – Steve Regan Company07 novembro 2024 -
 US financial institutions should remain vigilant for Russian attempts to evade US export controls say FinCEN and BIS – Association of Trade Finance Compliance Professionals07 novembro 2024
US financial institutions should remain vigilant for Russian attempts to evade US export controls say FinCEN and BIS – Association of Trade Finance Compliance Professionals07 novembro 2024 -
 Myths and Distortions from TikTok's Defenders Help It Evade Needed Accountability07 novembro 2024
Myths and Distortions from TikTok's Defenders Help It Evade Needed Accountability07 novembro 2024 -
 Sanctions and Export Controls, UK Regulatory Outlook November 2023 - Osborne Clarke07 novembro 2024
Sanctions and Export Controls, UK Regulatory Outlook November 2023 - Osborne Clarke07 novembro 2024
você pode gostar
-
 Best Reality Shows On Prime Video07 novembro 2024
Best Reality Shows On Prime Video07 novembro 2024 -
 Splitgate dev 1047 Games adds ex-Ubisoft, EA staff in key roles07 novembro 2024
Splitgate dev 1047 Games adds ex-Ubisoft, EA staff in key roles07 novembro 2024 -
 World's Most Powerful Passports Lose Value Due to Coronavirus - VisaGuide.News07 novembro 2024
World's Most Powerful Passports Lose Value Due to Coronavirus - VisaGuide.News07 novembro 2024 -
 Download do aplicativo Tiny Pou 2 2023 - Grátis - 9Apps07 novembro 2024
Download do aplicativo Tiny Pou 2 2023 - Grátis - 9Apps07 novembro 2024 -
 Hellen & Rafael, Sawnee Mountain Vow Renew07 novembro 2024
Hellen & Rafael, Sawnee Mountain Vow Renew07 novembro 2024 -
 Emiliano Sala sofreu intoxicação antes de morrer em acidente de avião07 novembro 2024
Emiliano Sala sofreu intoxicação antes de morrer em acidente de avião07 novembro 2024 -
Knockout City™ Block Party Edition07 novembro 2024
-
stillewillem: portrait of a businessman with a beard, 3dpeople, (gigachad :0.4)07 novembro 2024
-
Kit de Ferramentas Oficina para Motos 85 peças Gedore Ref. KMM-BPM-2 Cód. 084.55107 novembro 2024
-
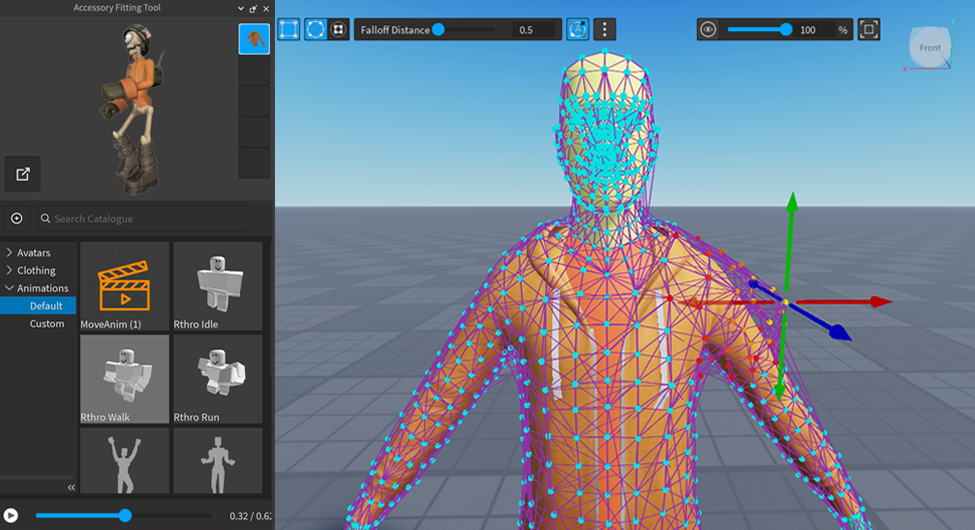 Accessory Fitting Tool Documentation - Roblox Creator Hub07 novembro 2024
Accessory Fitting Tool Documentation - Roblox Creator Hub07 novembro 2024

