SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 08 novembro 2024

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.
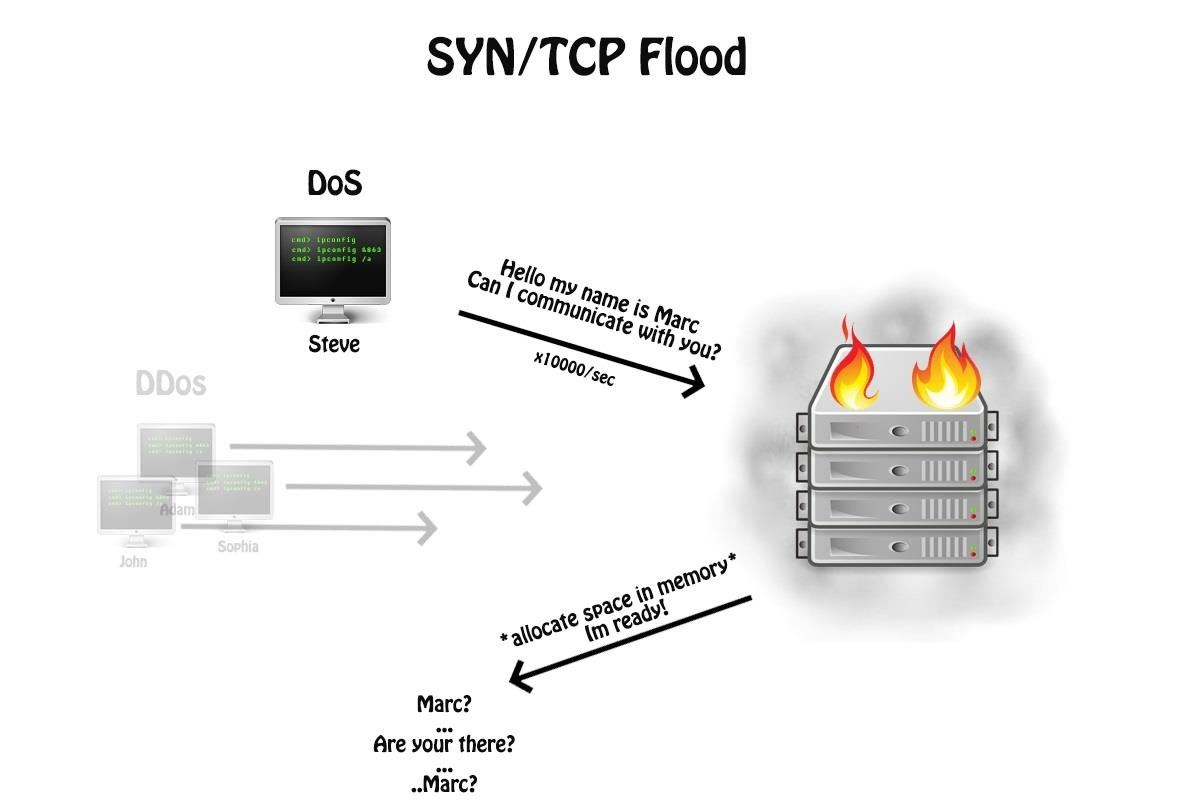
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 4 (Evading Detection While DoSing) « Null Byte :: WonderHowTo

Evading AV with Veil-Evasion

How Hackers Are “Blending In” to Evade Detection

SILKLOADER: How Hackers Evade Detection

Chinese Hackers Use New Cryptojacking Tactics to Evade Detection

hacking news, Breaking Cybersecurity News

HackerBox #0055 - High Roller – HackerBoxes

OSINTer - Article List

Chinese Silkloader cyber attack tool falls into Russian hands

Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection
Risky Biz News: Google wants to reduce lifespan of TLS certificates from one year to just 90 days

How Hackers Are “Blending In” to Evade Detection
Recomendado para você
-
 Blox Fruits Script Latest 2023 Download For Windows PC - Softlay08 novembro 2024
Blox Fruits Script Latest 2023 Download For Windows PC - Softlay08 novembro 2024 -
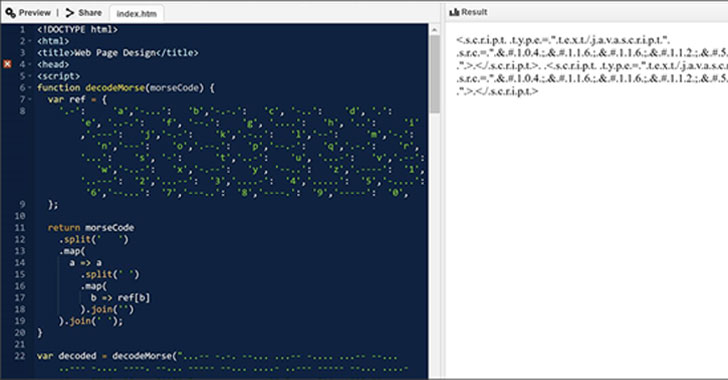 Hackers Spotted Using Morse Code in Phishing Attacks to Evade08 novembro 2024
Hackers Spotted Using Morse Code in Phishing Attacks to Evade08 novembro 2024 -
 Evade script - (Godmode, FullBright)08 novembro 2024
Evade script - (Godmode, FullBright)08 novembro 2024 -
![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg) OP Evade Script GUI [FREE]08 novembro 2024
OP Evade Script GUI [FREE]08 novembro 2024 -
 Evade Script Auto Farm Wins, Auto Random Vote & MORE08 novembro 2024
Evade Script Auto Farm Wins, Auto Random Vote & MORE08 novembro 2024 -
 Snippet of Server-side script generated by ChatGPT to evade08 novembro 2024
Snippet of Server-side script generated by ChatGPT to evade08 novembro 2024 -
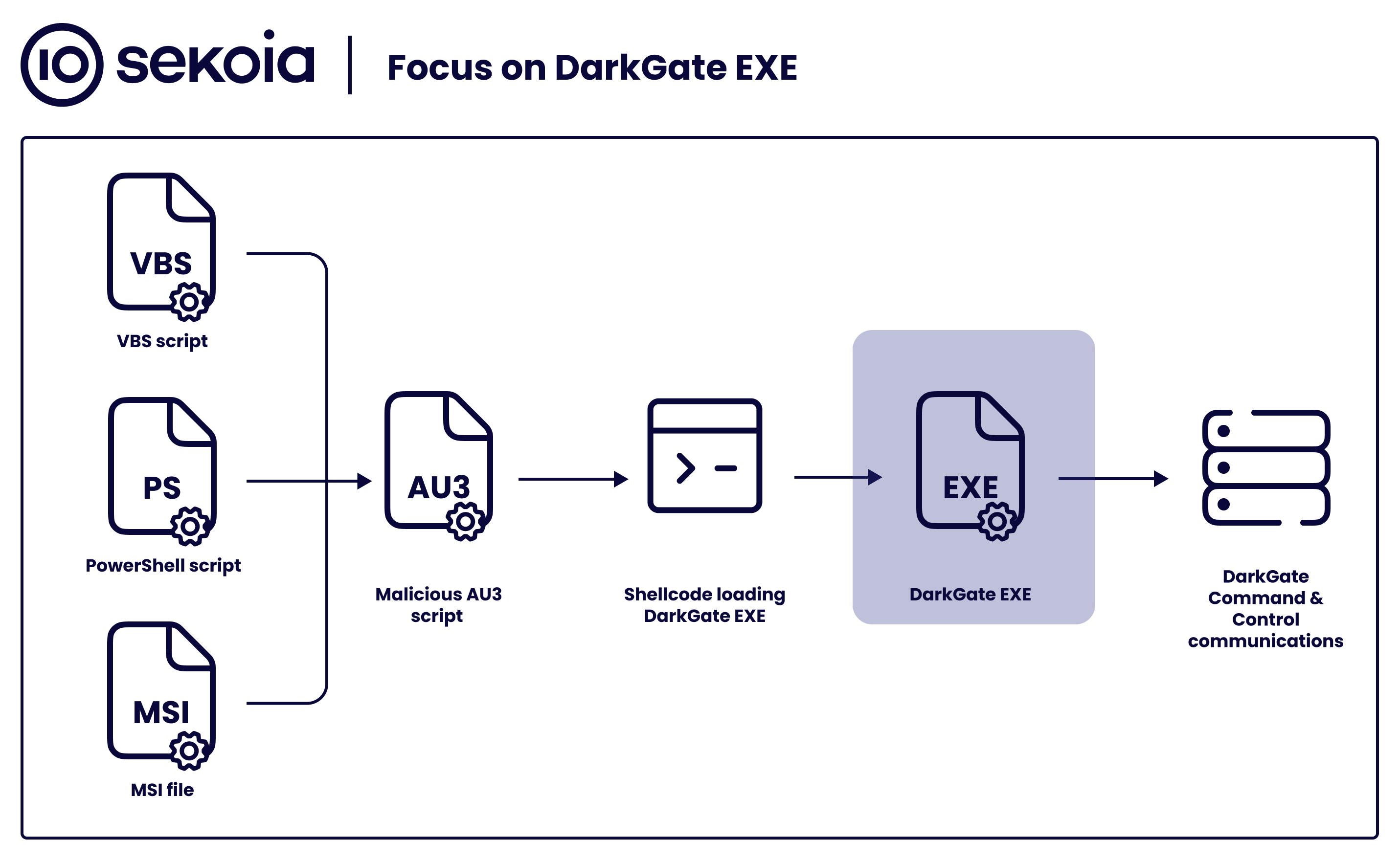
Sekoia.io on X: #DarkGate gained popularity among threat actors08 novembro 2024
-
 Obsidian Giant, Evolution Evade Wiki08 novembro 2024
Obsidian Giant, Evolution Evade Wiki08 novembro 2024 -
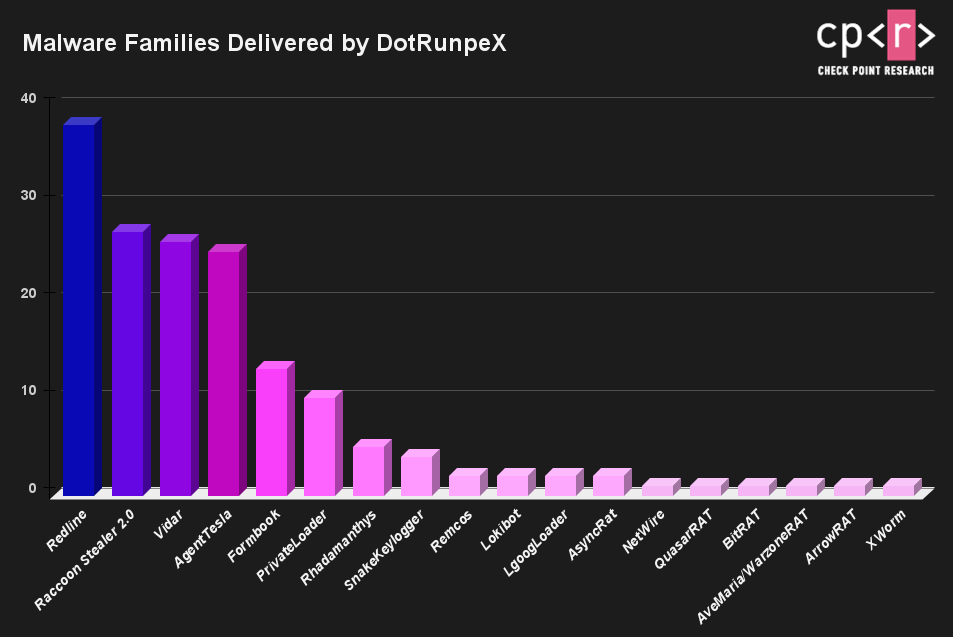
Winnti Hackers Split Cobalt Strike Into 154 Pieces To Evade Detection08 novembro 2024
-
 Evade Script - Summoner's Champion Information - League of Legends08 novembro 2024
Evade Script - Summoner's Champion Information - League of Legends08 novembro 2024
você pode gostar
-
 Topo de Bolo Decorativo 3D para Festa Princesas em EVA - 1 Un08 novembro 2024
Topo de Bolo Decorativo 3D para Festa Princesas em EVA - 1 Un08 novembro 2024 -
 A Plague Tale: Requiem review: gorgeous sequel has growing pains08 novembro 2024
A Plague Tale: Requiem review: gorgeous sequel has growing pains08 novembro 2024 -
 Free Download Computer Wallpaper HD for Desktop.08 novembro 2024
Free Download Computer Wallpaper HD for Desktop.08 novembro 2024 -
 170 ideias de Basketball em 2023 basquete, arte de basquete, basquete fotos08 novembro 2024
170 ideias de Basketball em 2023 basquete, arte de basquete, basquete fotos08 novembro 2024 -
 Game Settings and Download a Copy greyed out when focused on a08 novembro 2024
Game Settings and Download a Copy greyed out when focused on a08 novembro 2024 -
 Tonikaku Kawaii: SNS (TONIKAWA: Over The Moon For You - SNS)08 novembro 2024
Tonikaku Kawaii: SNS (TONIKAWA: Over The Moon For You - SNS)08 novembro 2024 -
 Jigsaw Puzzle Dreams no Steam08 novembro 2024
Jigsaw Puzzle Dreams no Steam08 novembro 2024 -
como sair do grupo do discord|Pesquisa do TikTok08 novembro 2024
-
 PaRappa the Rapper Remastered Is Actually Emulated, And Here's How It Was Done - Siliconera08 novembro 2024
PaRappa the Rapper Remastered Is Actually Emulated, And Here's How It Was Done - Siliconera08 novembro 2024 -
 The Doors of Stone - Poems 1938-1962 by Prince, F.T.: Fine Hardcover (1963) 1st Edition, Inscribed by Author(s)08 novembro 2024
The Doors of Stone - Poems 1938-1962 by Prince, F.T.: Fine Hardcover (1963) 1st Edition, Inscribed by Author(s)08 novembro 2024